Preventing Cross-Site Scripting in websites
Preventing Cross-Site Scripting (XSS) attacks is crucial for maintaining the security of your website. Here's an in-depth guide on how you can do this:
Validate input
Input validation is the process of ensuring that the input provided by the user is of the correct type, size, and format before it is processed. This is an important step in preventing XSS attacks as it ensures that no malicious scripts are injected into the input. It can be done by applying the following:
Use a Whitelist: The simplest form of input validation is to use a whitelist. This means only allowing certain types of input and rejecting everything else. For example, if you're expecting a number, you should reject any input that contains letters or special characters.
Escape Special Characters: Another method is to escape special characters that have a special meaning in HTML, XML, or JavaScript. For example, you can replace < with < and > with >.
Regular Expressions: Regular expressions can be used to validate more complex patterns. For example, you can use a regular expression to ensure that an input matches a certain format, such as a phone number or an email address.
Validate output
Output validation is the process of validating the output that is sent to the client's browser. This is an important step in preventing XSS attacks as it ensures that no malicious scripts are included in the output. It can be done by applying the following:
Use Context-Specific Output Encoding: This should be used in all HTML, XML, JavaScript, and CSS contexts to protect from XSS. For example, you can use the htmlspecialchars function in PHP to escape special characters in HTML.
Use a Framework or Library: Many programming languages have frameworks or libraries that can help with output validation. For example, the OWASP ESAPI provides a set of encoding functions for various types of output.
Regular Expressions: Regular expressions can be used to validate more complex patterns. For example, you can use a regular expression to ensure that an output matches a certain format, such as a phone number or an email address.
Content Security Policy
Content Security Policy (CSP) is an added layer of security that helps to detect and mitigate certain types of attacks, including Cross-Site Scripting (XSS) and data injection attacks. It's a security layer that helps you detect and mitigate certain types of attacks, including Cross Site Scripting (XSS) and data injection attacks. These attacks are used for everything from data theft to site defacement or distribution of malware.
A CSP is a set of rules that you can set up on the server to tell the browser which domains the browser should consider to be valid sources of executable scripts. The browser then uses these rules to decide whether to execute a script or not.
For example, the following Content Security Policy directive tells the browser to only execute scripts that are loaded from the current domain:
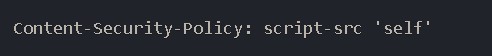 This means that even if an attacker manages to inject a malicious script into your website, the browser will refuse to execute it because it's not from the same domain specified in the CSP.
In addition to preventing XSS attacks, a CSP can also help you detect and mitigate other types of attacks, such as data injection attacks. For example, you can set up a CSP to tell the browser to only load images from a certain domain, which can help you prevent attacks where an attacker tries to trick a user into loading a malicious image.
Remember, a CSP is not a replacement for good input validation and output encoding, but it's a valuable addition to your security toolbox.
This means that even if an attacker manages to inject a malicious script into your website, the browser will refuse to execute it because it's not from the same domain specified in the CSP.
In addition to preventing XSS attacks, a CSP can also help you detect and mitigate other types of attacks, such as data injection attacks. For example, you can set up a CSP to tell the browser to only load images from a certain domain, which can help you prevent attacks where an attacker tries to trick a user into loading a malicious image.
Remember, a CSP is not a replacement for good input validation and output encoding, but it's a valuable addition to your security toolbox.
Genesis 32:10
I am not worthy of the least of all the deeds of steadfast love and all the faithfulness that you have shown to your servant, for with only my staff I crossed this Jordan, and now I have become two camps.

